Happy holidays everyone! This November Iain and I worked together on Stem’s descriptor capabilities. Though this won’t be of interest to a general audience, for metrics folks like us these are pretty neat.
Descriptor Digesting
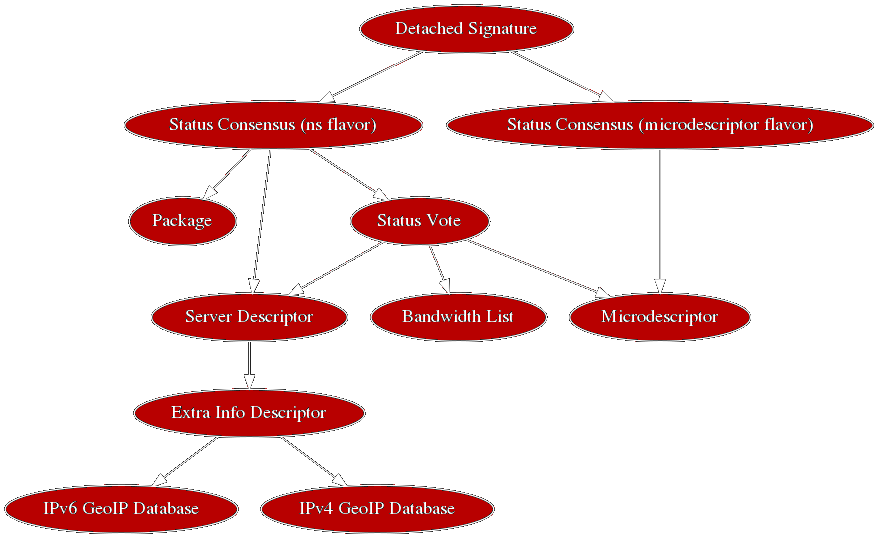
Tor relay information is provided by multiple documents. Signed descriptors transitively validate others by inclusion of their digest. For example, our consensus references server descriptor digest, and server descriptors in turn cite extrainfo digests.
To illustrate, here’s a diagram from Iain…
Stem can now calculate digests from server, extrainfo, microdescriptor, and consensus documents. For instance, to validate an extrainfo descriptor…
import sys
import stem.descriptor.remote
import stem.util.tor_tools
def download_descriptors(fingerprint):
"""
Downloads the descriptors we need to validate this relay. Downloads are
parallelized, providing the caller with a tuple of the form...
(router_status_entry, server_descriptor, extrainfo_descriptor)
"""
conensus_query = stem.descriptor.remote.get_consensus()
server_desc_query = stem.descriptor.remote.get_server_descriptors(fingerprint)
extrainfo_query = stem.descriptor.remote.get_extrainfo_descriptors(fingerprint)
router_status_entries = filter(lambda desc: desc.fingerprint == fingerprint, conensus_query.run())
if len(router_status_entries) != 1:
raise IOError("Unable to find relay '%s' in the consensus" % fingerprint)
return (
router_status_entries[0],
server_desc_query.run()[0],
extrainfo_query.run()[0],
)
if __name__ == '__main__':
fingerprint = raw_input("What relay fingerprint would you like to validate?\n")
print('') # blank line
if not stem.util.tor_tools.is_valid_fingerprint(fingerprint):
print("'%s' is not a valid relay fingerprint" % fingerprint)
sys.exit(1)
try:
router_status_entry, server_desc, extrainfo_desc = download_descriptors(fingerprint)
except Exception as exc:
print(exc)
sys.exit(1)
if router_status_entry.digest == server_desc.digest():
print("Server descriptor digest is correct")
else:
print("Server descriptor digest invalid, expected %s but is %s" % (router_status_entry.digest, server_desc.digest()))
if server_desc.extra_info_digest == extrainfo_desc.digest():
print("Extrainfo descriptor digest is correct")
else:
print("Extrainfo descriptor digest invalid, expected %s but is %s" % (server_desc.extra_info_digest, extrainfo_desc.digest()))
python demo.py What relay fingerprint would you like to validate? 3BB34C63072D9D10E836EE42968713F7B9325F66 Server descriptor digest is correct Extrainfo descriptor digest is correct
Detached Signatures
Somewhat obscure, detached signatures are exchanged among directory authorites to establish the next hour’s consensus. They reference the agreed upon digest the consensus should have, and are only available five minutes of every hour (minutes 55-60). Stem can now read these documents…
import stem.descriptor.remote
detached_sigs = stem.descriptor.remote.get_detached_signatures().run()[0]
for i, sig in enumerate(detached_sigs.signatures):
print('Signature %i is from %s' % (i + 1, sig.identity))
When available (minutes 55-60 of the hour)
% python demo.py Signature 1 is from 0232AF901C31A04EE9848595AF9BB7620D4C5B2E Signature 2 is from 14C131DFC5C6F93646BE72FA1401C02A8DF2E8B4 Signature 3 is from 23D15D965BC35114467363C165C4F724B64B4F66 Signature 4 is from 27102BC123E7AF1D4741AE047E160C91ADC76B21 Signature 5 is from 49015F787433103580E3B66A1707A00E60F2D15B Signature 6 is from D586D18309DED4CD6D57C18FDB97EFA96D330566 Signature 7 is from E8A9C45EDE6D711294FADF8E7951F4DE6CA56B58 Signature 8 is from ED03BB616EB2F60BEC80151114BB25CEF515B226 Signature 9 is from EFCBE720AB3A82B99F9E953CD5BF50F7EEFC7B97
When unavailable (minutes 0-55 of the hour)
% python demo.py Traceback (most recent call last): File "demo.py", line 3, indetached_sigs = stem.descriptor.remote.get_detached_signatures().run()[0] File "/home/atagar/Desktop/stem/stem/descriptor/remote.py", line 476, in run return list(self._run(suppress)) File "/home/atagar/Desktop/stem/stem/descriptor/remote.py", line 487, in _run raise self.error urllib2.HTTPError: HTTP Error 404: Not found